-->
The WindowsApps folder is located on the operating system drive under the Program Files directory. The most common path to that folder is: C:Program FilesWindowsApps. This folder is hidden, so you need to enable hidden files in File Explorer. Even when visible, the permissions pre-configured for this folder do not allow the user to open it.
Going over getting IPP to work with the Windows 10 iTunes. Jul 08, 2020. Mar 11, 2018.
This article provides a deeper dive on what happens to files and registry entries when you create a Windows app package for your desktop application.
A key goal of a modern package is to separate application state from system state as much as possible while maintaining compatibility with other apps. Windows 10 accomplishes this by placing the application inside a MSIX package, and then detecting and redirecting some changes it makes to the file system and registry at runtime.
Packages that you create for your desktop application are desktop-only, full-trust applications and are not virtualized or sandboxed. This allows them to interact with other apps the same way classic desktop applications do.
Installation
App packages are installed under C:Program FilesWindowsAppspackage_name, with the executable titled app_name.exe. Each package folder contains a manifest (named AppxManifest.xml) that contains a special XML namespace for packaged apps. Inside that manifest file is an <EntryPoint> element, which references the full-trust app. When that application is launched, it does not run inside an app container, but instead it runs as the user as it normally would.
After deployment, package files are marked read-only and heavily locked down by the operating system. Windows prevents apps from launching if these files are tampered with.
File system
The OS supports different levels of file system operations for packaged desktop applications, depending on the folder location.
AppData operations on Windows 10, version 1903 and later
All newly created files and folders in the user's AppData folder (e.g., C:Usersuser_nameAppData) are written to a private per-user, per-app location but merged at runtime to appear in the real AppData location. This allows some degree of state separation for artifacts that are only used by the application itself, and this enables the system to clean up those files when the application is uninstalled. Modifications to existing files under the user's AppData folder is allowed to provide a higher degree of compatibility and interactivity between applications and the OS. This reduces filesystem “rot” because the OS is aware of every file or directory change made by an application. State separation also allows packaged desktop applications to pick up where a non-packaged version of the same application left off. Note that the OS does not support a virtual file system (VFS) folder for the user's AppData folder.
AppData operations on Windows 10, version 1809 and earlier
All writes to the user's AppData folder (e.g., C:Usersuser_nameAppData), including create, delete, and update, are copied on write to a private per-user, per-app location. This creates the illusion that the packaged application is editing the real AppData when it is actually modifying a private copy. By redirecting writes this way, the system can track all file modifications made by the app. This allows the system to clean up those files when the application is uninstalled, thus reducing system 'rot' and providing a better application removal experience for the user.
Other folders
In addition to redirecting AppData, Windows' well-known folders (System32, Program Files (x86), etc) are dynamically merged with corresponding directories in the app package. Each package contains a folder named 'VFS' at its root. Any reads of directories or files in the VFS directory are merged at runtime with their respective native counterparts. For example, an application could contain C:Program FilesWindowsAppspackage_nameVFSSystemX86vc10.dll as part of its app package, but the file would appear to be installed at C:WindowsSystem32vc10.dll. This maintains compatibility with desktop applications that may expect files to live in non-package locations.
Writes to files/folders in the app package are not allowed. Writes to files and folders that are not part of the package are ignored by the OS and are allowed as long as the user has permission.
Common operations
This short reference table shows common file system operations and how the OS handles them.
| Operation | Result | Example |
|---|---|---|
| Read or enumerate a well-known Windows file or folder | A dynamic merge of C:Program Filespackage_nameVFSwell_known_folder with the local system counterpart. | Reading C:WindowsSystem32 returns the contents of C:WindowsSystem32 plus the contents of C:Program FilesWindowsAppspackage_nameVFSSystemX86. |
| Write under AppData | Windows 10, version 1903 and later: New files and folders created under the following directories are redirected to a per-user, per-package private location:
Windows 10, version 1809 and earlier: Copy-on-written to a per-user, per-app location. | AppData is typically C:Usersuser_nameAppData. |
| Write inside the package | Not allowed. The package is read-only. | Writes under C:Program FilesWindowsAppspackage_name are not allowed. |
| Writes outside the package | Allowed if the user has permissions. | A write to C:WindowsSystem32foo.dll is allowed if the package does not contain C:Program FilesWindowsAppspackage_nameVFSSystemX86foo.dll and the user has permissions. |
Packaged VFS locations
The following table shows where files shipping as part of your package are overlaid on the system for the app. Your application will perceive these files to be in the listed system locations, when in fact they are in the redirected locations inside C:Program FilesWindowsAppspackage_nameVFS. The FOLDERID locations are from the KNOWNFOLDERID constants.
| System Location | Redirected Location (Under [PackageRoot]VFS) | Valid on architectures |
|---|---|---|
| FOLDERID_SystemX86 | SystemX86 | x86, amd64 |
| FOLDERID_System | SystemX64 | amd64 |
| FOLDERID_ProgramFilesX86 | ProgramFilesX86 | x86, amd6 |
| FOLDERID_ProgramFilesX64 | ProgramFilesX64 | amd64 |
| FOLDERID_ProgramFilesCommonX86 | ProgramFilesCommonX86 | x86, amd64 |
| FOLDERID_ProgramFilesCommonX64 | ProgramFilesCommonX64 | amd64 |
| FOLDERID_Windows | Windows | x86, amd64 |
| FOLDERID_ProgramData | Common AppData | x86, amd64 |
| FOLDERID_Systemcatroot | AppVSystem32Catroot | x86, amd64 |
| FOLDERID_Systemcatroot2 | AppVSystem32Catroot2 | x86, amd64 |
| FOLDERID_Systemdriversetc | AppVSystem32DriversEtc | x86, amd64 |
| FOLDERID_Systemdriverstore | AppVSystem32Driverstore | x86, amd64 |
| FOLDERID_Systemlogfiles | AppVSystem32Logfiles | x86, amd64 |
| FOLDERID_Systemspool | AppVSystem32Spool | x86, amd64 |
Registry
App packages contain a registry.dat file, which serves as the logical equivalent of HKLMSoftware in the real registry. At runtime, this virtual registry merges the contents of this hive into the native system hive to provide a singular view of both. For example, if registry.dat contains a single key 'Foo', then a read of HKLMSoftware at runtime will also appear to contain 'Foo' (in addition to all the native system keys).
Only keys under HKLMSoftware are part of the package; keys under HKCU or other parts of the registry are not. Writes to keys or values in the package are not allowed. Writes to keys or values not part of the package are allowed as long as the user has permission.
All writes under HKCU are copy-on-written to a private per-user, per-app location. Traditionally, uninstallers are unable to clean HKEY_CURRENT_USER because the registry data for logged out users is unmounted and unavailable.
All writes are kept during package upgrade and only deleted when the application is removed entirely.
Common operations
This short reference table shows common registry operations and how the OS handles them.
| Operation | Result | Example |
|---|---|---|
| Read or enumerate HKLMSoftware | A dynamic merge of the package hive with the local system counterpart. | If registry.dat contains a single key 'Foo,' at runtime a read of HKLMSoftware will show the contents of both HKLMSoftware plus HKLMSoftwareFoo. |
| Writes under HKCU | Copy-on-written to a per-user, per-app private location. | The same as AppData for files. |
| Writes inside the package. | Not allowed. The package is read-only. | Writes under HKLMSoftware are not allowed if a corresponding key/value exist in the package hive. |
| Writes outside the package | Ignored by the OS. Allowed if the user has permissions. | Writes under HKLMSoftware are allowed as long as a corresponding key/value does not exist in the package hive and the user has the correct access permissions. |
Uninstallation
When a package is uninstalled by the user, all files and folders located under C:Program FilesWindowsAppspackage_name are removed, as well as any redirected writes to AppData or the registry that were captured during the packaging process.
WindowsApps is a special folder where Windows 10 keeps installed apps from the Store. If some day you need to explore its contents to troubleshoot any issues, you'll face the problem that you have no access to the folder. Here is how to resolve the issue.
This folder is hidden, so you need to enable hidden files in File Explorer. Even when visible, the permissions pre-configured for this folder do not allow the user to open it. Once you open it, an error message appears 'You have been denied permission to access this folder'. If you want to access the WindowsApps folder, you need to adjust its file system permissions. This will require a number of steps from you. You must be signed in with an administrative account to continue.
To open the WindowsApps folder in Windows 10, do the following.
Open the Program files folder (the parent folder of WindowsApps) in File Explorer.
Find the WindowsApps folder in the list. If it is not visible, enable hidden files in File Explorer.
Windowsapps Folder Permission
Now, right-click the WindowsApps folder and select Properties from the context menu.
In the Properties dialog window, go to the Security tab. There you'll see the button Advanced. Click it.
In the next dialog, click the link Change under Owner. You might be asked to enter the password of the Administrator account. Type it when prompted.
Select the Administrators group as the new owner. Click OK.
Windowsapps Directory
Tick the checkbox 'Replace owner on subcontainers and objects' and click Apply.

This should be enough to browse the contents of the folder. Open the folder and confirm the UAC prompt:
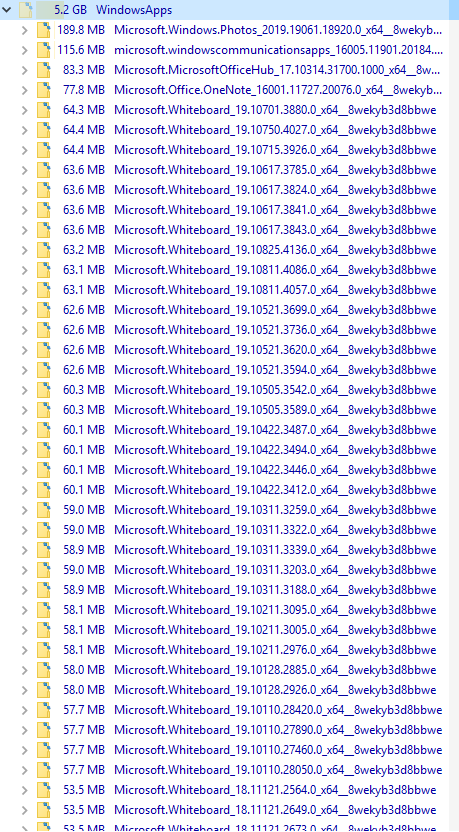
The folder contents will be accessible:
Please keep in mind that file operations in this folder can break installed Store apps and make them unusable. Do not delete or change anything in this folder unless you know exactly what you are doing.
Advertisment